The pro hacker starter kit
Everything You Need to Start Hacking - Without the Hours of Trial and Error!
Get instant access to the EXACT commands, techniques, and methods
that professional hackers use daily.
Stop wasting time with outdated YouTube tutorials and random forum posts.
The Pro Hacker Starter Kit gives you the exact workflows, one-liner commands, and tactics pros use every day — organized, explained, and ready to use.⏱️
Whether you’re starting out or leveling up your skills, this bundle is your secret shortcut to hacking smarter, faster, and with more confidence than ever before.
$149 $19.99
Unlock The Pro Hacker Starter KitMaster Every Phase of a Real-World Hack
The Pro Hacker Starter Kit walks you through the tools, commands, and tactics for every stage — from recon to reporting — so you’re never guessing what comes next.
🔍 Reconnaissance
Gathering information about the target to identify potential entry points.
Key Points:
- Identify open ports and running services
- Discover subdomains and network topology
- Gather employee information and email addresses
- Map the attack surface
Sample Commands:
nmap -sV -sC -p- [target]
theharvester -d [domain] -b google
whois [domain]
dig [domain] any
🛡️ Vulnerability Analysis
Identifying weaknesses in the target system that can be exploited.
Key Points:
- Scan for known vulnerabilities
- Analyze software versions and configurations
- Identify misconfigurations
- Prioritize vulnerabilities based on severity
Sample Commands:
nmap --script vuln [target]
nikto -h [target]
openvas-start
dirb http://[target]
💻 Exploitation
Using identified vulnerabilities to gain unauthorized access.
Key Points:
- Develop or use existing exploits
- Bypass security controls
- Gain initial access to the system
- Escalate privileges if needed
Sample Commands:
msfconsole
use exploit/[exploit-name]
set RHOST [target]
exploit
🔧 Post Exploitation
Maintaining access and gathering more data after initial compromise.
Key Points:
- Establish persistence
- Extract sensitive data
- Move laterally within the network
- Cover tracks to avoid detection
Sample Commands:
net user [username] [password] /add
reg add HKLM\Software\Microsoft\Windows\CurrentVersion\Run
mimikatz "sekurlsa::logonpasswords"
net view
📊 Reporting
Documenting findings and providing actionable recommendations.
Key Points:
- Detail vulnerabilities and exploits used
- Assess the impact of the breach
- Provide remediation steps
- Present findings to stakeholders
Sample Tools:
Dradis
Metasploit Pro (Reporting)
Custom Scripts (e.g., Python)
LaTeX for Professional Reports
Every Tool, Command, and Workflow You Need To
Start Hacking Like A Pro
This isn’t just theory — each module gives you real commands, tested workflows, and pro-level insights you won’t find by Googling for hours.
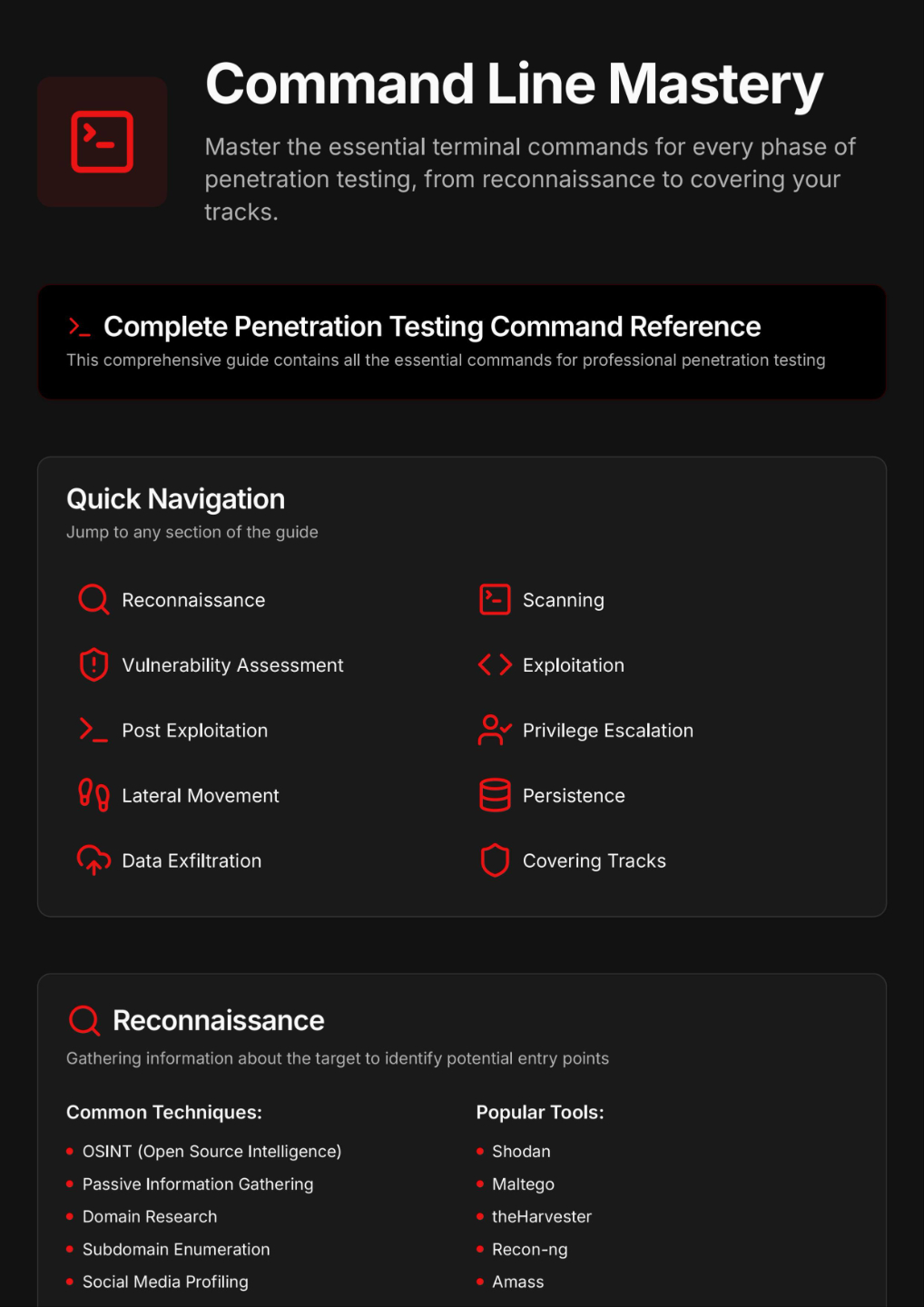
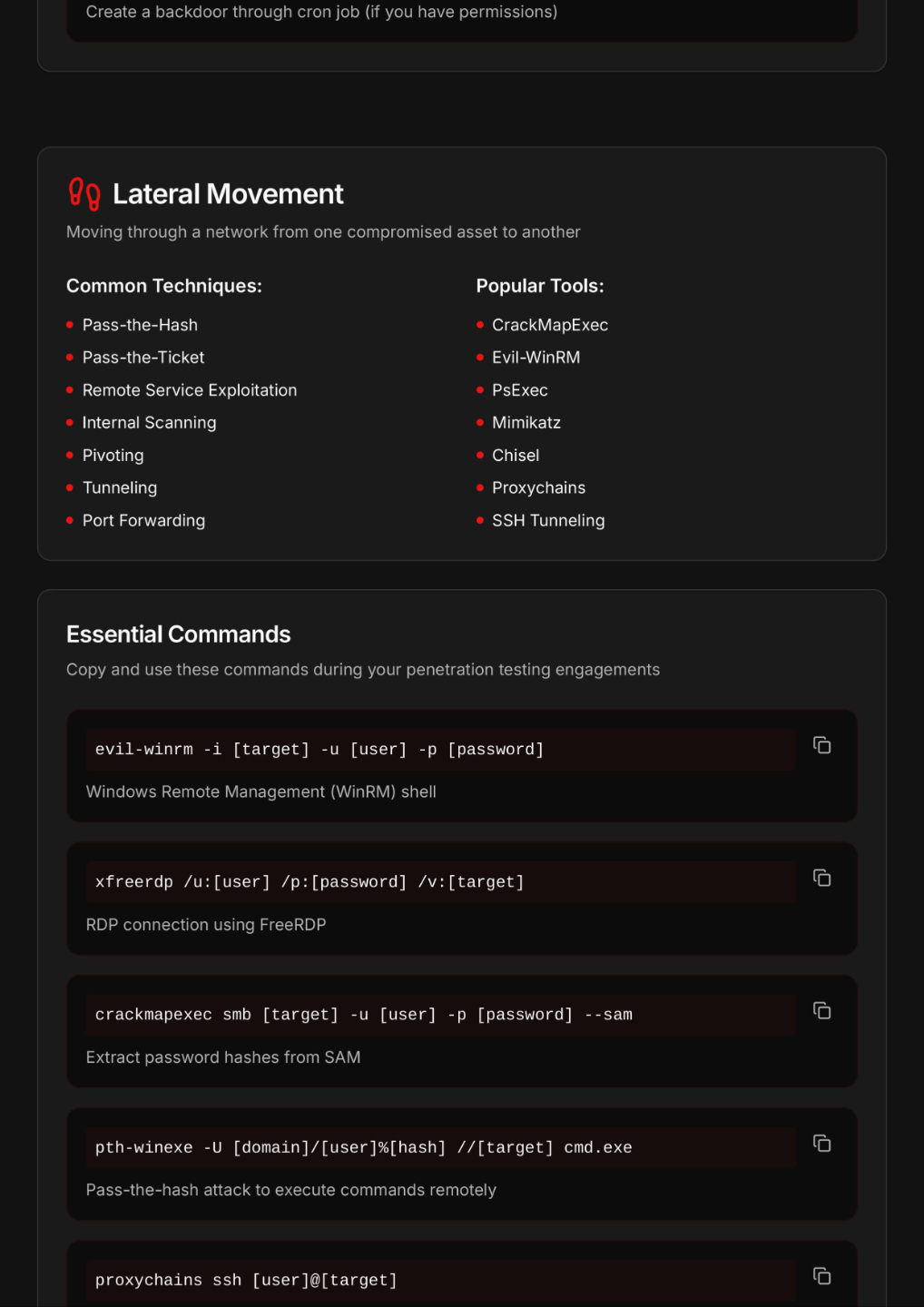
Command Line Mastery
Learn essential terminal commands and techniques that hackers use to navigate systems and execute powerful attacks.
Privilege Escalation
Discover methods to gain higher access levels in Windows and Linux systems through proven exploitation paths.
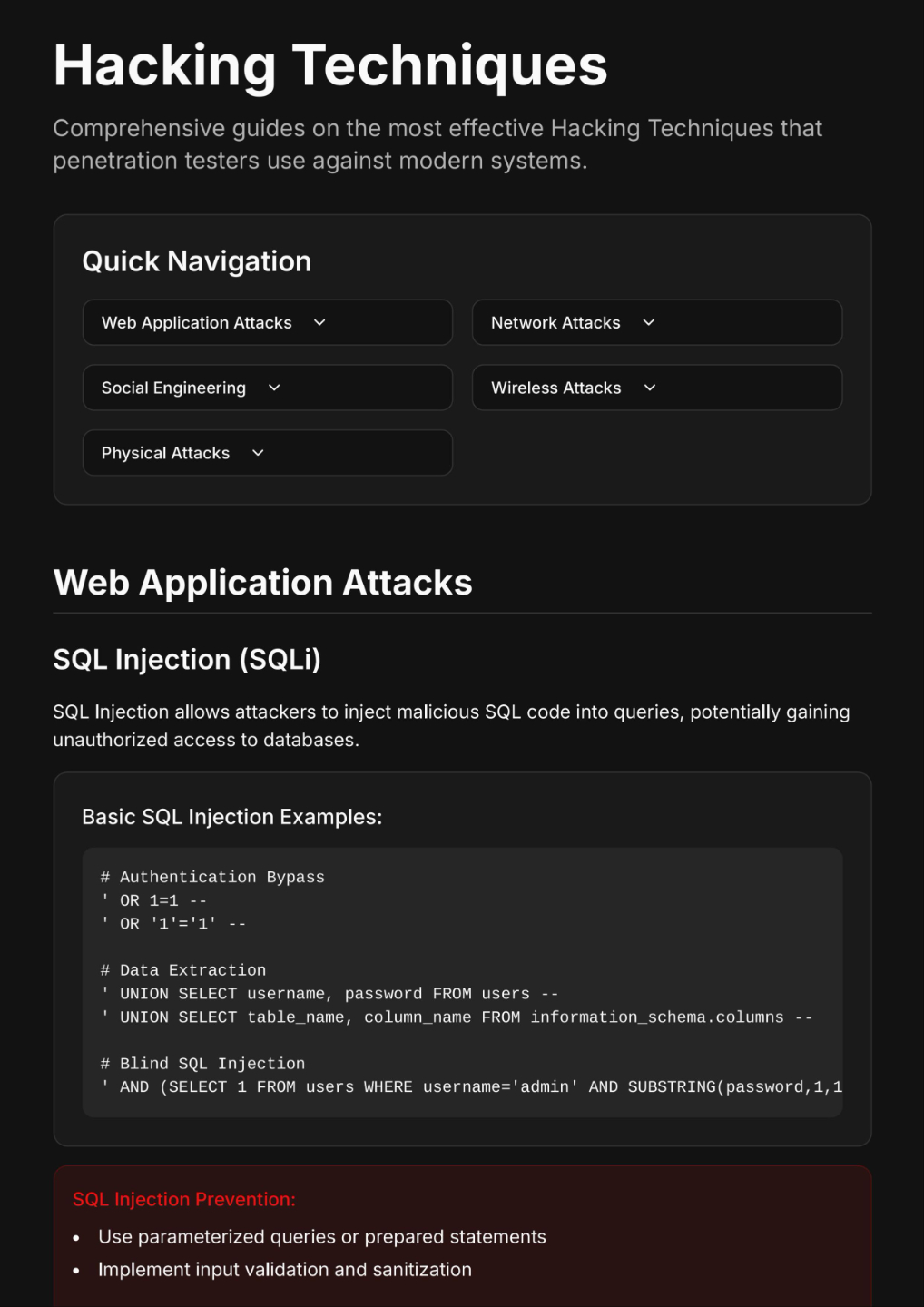
Hacking Techniques
Comprehensive guides on the most effective attack vectors that penetration testers use against modern systems.
Reverse Shell Techniques
Master the art of establishing remote access with detailed one-liners and payload configurations for every scenario.
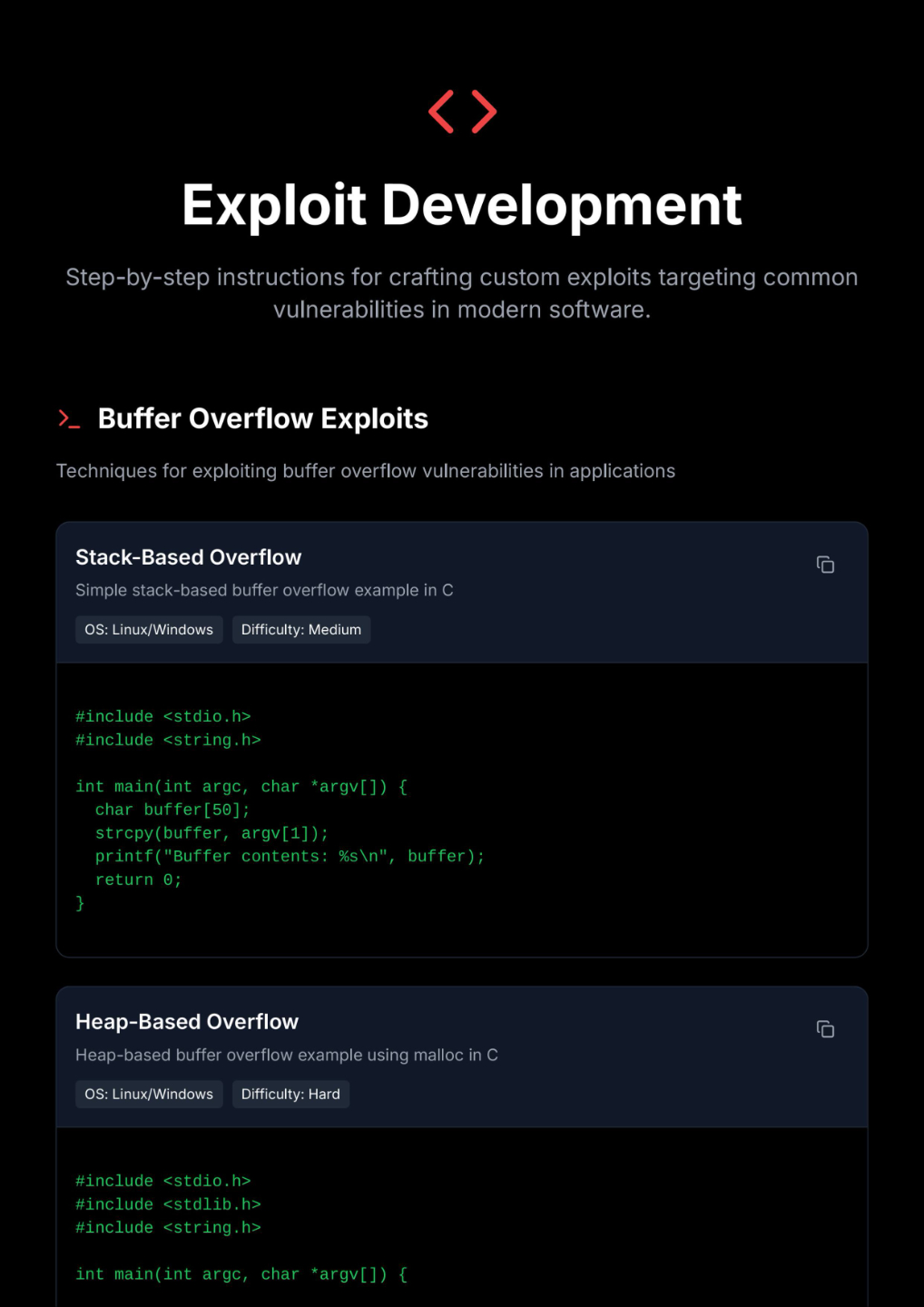
Exploit Development
Step-by-step instructions for crafting custom exploits targeting common vulnerabilities in modern software.
Comprehensive Resources
From reconnaissance to post-exploitation, access complete resources covering the entire ethical hacking methodology.
Your Arsenal of Hacking Resources
(A Sneek Peek)


“This Kit Changed Everything for Me.”
"This Kit Changed Everything for Me. The tool breakdowns are pure gold!"
Alex R. - Ethical Hacker
"Incredible commands and real-world examples. My only gripe is I wanted even more mobile hacking tips!"
Sam K. - Tech Guy
"Hands down the best hacking resource out there. It’s like having a pro mentor in my pocket."
Jamie L. - Cybersecurity Student
What You'll Unlock Today
- 6 Cheatsheets (70+ pages) that cut out the fluff and show only what works
- Full Hacking Guide to walk you through every phase (from Recon to Reporting)
- Hacker’s Checklist for stress-free pen testing
- All files in searchable, printable PDF format for easy use in the field
Transform How You Learn Hacking (Immediately)
- Save 100+ hours of research and trial-and-error
- Pass security certifications (OSCP, CEH, PNPT) Easier
- Execute successful penetration tests with confidence
- Impress employers with practical security skills
Instant Access
Start downloading within seconds after checkout
Proven Results
500+ hackers use these tools daily
Risk-Free Purchase
30-day guarantee. No questions asked.
Got Questions? We've Got You Covered.
What exactly do I get when I buy the Pro Hacker Starter Kit?
I’m new to hacking — will this be too advanced?
How will I receive the materials?
Are these techniques legal to use?
Do you offer a money-back guarantee?
Will I get updates to the materials?
How is this different from free YouTube videos?
© 2025 Privacy Matters. All rights reserved. Unauthorized reproduction or distribution is strictly prohibited.
If you have any questions or need help, reach out to support on discord!
These resources are for educational purposes only.


